Recently it was announced that Apple will no longer offer patches and will end support for QuickTime for Windows, their multimedia software package for the Microsoft OS. This move came about shortly after several vulnerabilities were detected in the software. For over five years, Windows has supported popular media formats, such as H.264 and AAC, that were enabled by the installation of Quicktime. Also, all Windows web browsers support online video without the need for plug-ins like QuickTime. Due to these new vulnerabilities, the lack of need for QuickTime for video, and the fact that Apple will not patch the software, OIT is moving to disable QuickTime for Windows on all SMU managed Windows computers starting on June 14th.
Recently it was announced that Apple will no longer offer patches and will end support for QuickTime for Windows, their multimedia software package for the Microsoft OS. This move came about shortly after several vulnerabilities were detected in the software. For over five years, Windows has supported popular media formats, such as H.264 and AAC, that were enabled by the installation of Quicktime. Also, all Windows web browsers support online video without the need for plug-ins like QuickTime. Due to these new vulnerabilities, the lack of need for QuickTime for video, and the fact that Apple will not patch the software, OIT is moving to disable QuickTime for Windows on all SMU managed Windows computers starting on June 14th.
For those using video software that requires QuickTime being installed on Windows to enable video codecs, most notably Apple ProRes, this move might affect your workflow. Adobe has been working to remove the dependency on QuickTime for the past couple of years, and their software will now run without the need for QuickTime for Windows. The Abobe Creative Cloud Team had been working to support the missing codecs and only last month was able to announce the support for the native reading of ProRes. The fixes will soon be included in updates to the relevant Creative Cloud software. More information will be on the Creative Cloud blog as it becomes available.
If you need to remove QuickTime for Windows from your home computer, follow the instructions for uninstalling QuickTime 7 for Windows on the Apple support site.
For more information, please see below:
Note: This move will not affect Macintosh OS computers, only Windows OS computers.


 Apple just released the iOS 9.3.3 update, the final version for iOS 9 before the
Apple just released the iOS 9.3.3 update, the final version for iOS 9 before the  On Tuesday, July 2, SMU implemented a new feature as part of our anti-spam defense to rewrites web links considered questionable, included in inbound emails. The purpose of the rewrite is to prevent phishing and malware scams by forwarding certain web requests to a proxy service for analysis. While some benign links might be overwritten, the service protects against “zero-hour” exploits where the threat could be unknown. If a link is still considered suspect at the time it is clicked, the you will receive a prompt to either decline or proceed to the website in question.
On Tuesday, July 2, SMU implemented a new feature as part of our anti-spam defense to rewrites web links considered questionable, included in inbound emails. The purpose of the rewrite is to prevent phishing and malware scams by forwarding certain web requests to a proxy service for analysis. While some benign links might be overwritten, the service protects against “zero-hour” exploits where the threat could be unknown. If a link is still considered suspect at the time it is clicked, the you will receive a prompt to either decline or proceed to the website in question. Recently
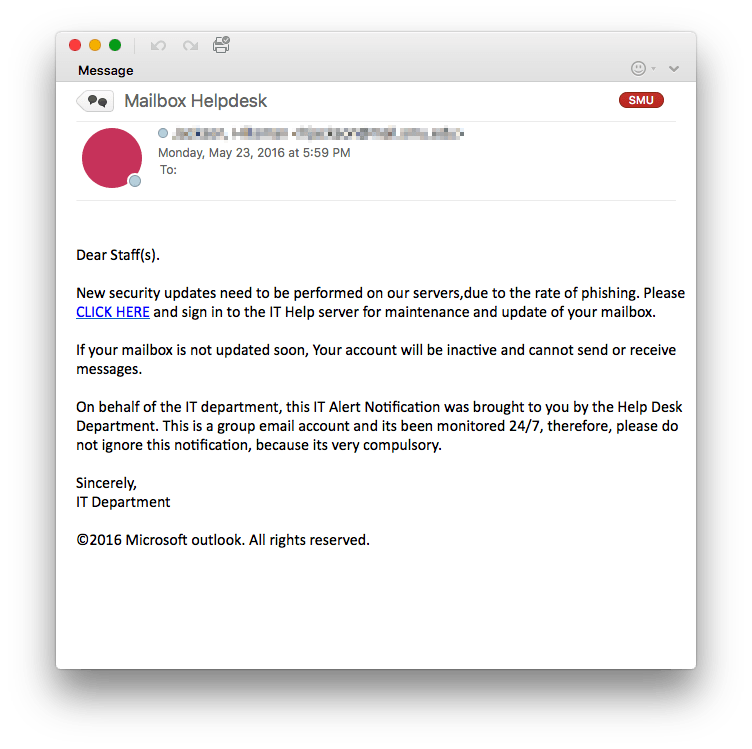
Recently  Another phishing email just hit a number of SMU email addresses. The message asks you to sign in to the Help Desk server for maintenance. It is sent from an address that is listed as the “Mailbox Helpdesk”. This is not a legitimate message.
Another phishing email just hit a number of SMU email addresses. The message asks you to sign in to the Help Desk server for maintenance. It is sent from an address that is listed as the “Mailbox Helpdesk”. This is not a legitimate message.