Originally featured in OIT’s Spring 2018 Security Report
Privacy is Dead
 It’s probably not the first time you’ve heard this. A private investigator, Sam Rambam was quoted as saying “Privacy is Dead – Get Over it” in 2006. In 2012, Huffing Post contributor Miles Feldman posed the question “Is Privacy Dead?” If it is, then our inheritance may have been in probate for years without us knowing it. The most recent major violation of privacy comes through a Facebook developer, Cambridge Analytica (discussed later in this newsletter), who collected data on millions of Americans without their consent to help political strategists win the 2016 US Presidential Election. But most likely this is only the tip of the iceberg. Continue reading Privacy Is Dead, Now Where’s My Inheritance
It’s probably not the first time you’ve heard this. A private investigator, Sam Rambam was quoted as saying “Privacy is Dead – Get Over it” in 2006. In 2012, Huffing Post contributor Miles Feldman posed the question “Is Privacy Dead?” If it is, then our inheritance may have been in probate for years without us knowing it. The most recent major violation of privacy comes through a Facebook developer, Cambridge Analytica (discussed later in this newsletter), who collected data on millions of Americans without their consent to help political strategists win the 2016 US Presidential Election. But most likely this is only the tip of the iceberg. Continue reading Privacy Is Dead, Now Where’s My Inheritance

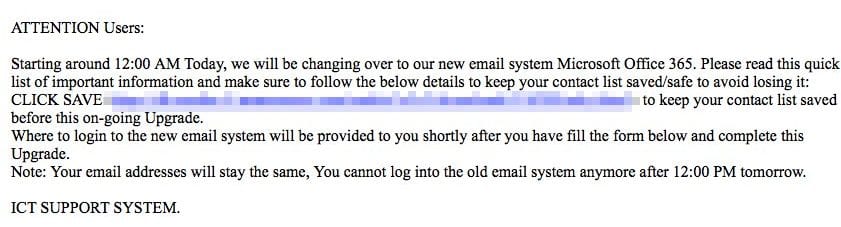
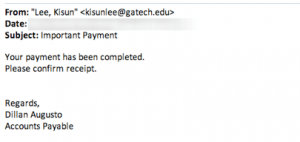
 Phishing is a method of identity theft which requests confidential information such as usernames, account numbers, passwords, etc. by masquerading as a legitimate, trusted company. This term typically refers to attempts through email. However, this same type of attack can occur in person (social engineering) or over the phone (farming).
Phishing is a method of identity theft which requests confidential information such as usernames, account numbers, passwords, etc. by masquerading as a legitimate, trusted company. This term typically refers to attempts through email. However, this same type of attack can occur in person (social engineering) or over the phone (farming).