Microsoft is discontinuing support for and replacing Forefront, our licensed anti-virus application for SMU Windows machines, with a solution called Endpoint Protection. OIT will begin deploying this replacement product via LANDesk over the next several weeks.
About Endpoint Protection
Endpoint Protection provides anti-virus and anti-malware protection, detection and remediation capabilities. The agent runs in the background and daily scans to ensure your computer is free from malware. If malware is present, it will attempt to clean it. Machines that cannot automatically clean will appear on a report monitored by OIT. A consultant is then dispatched to remediate the malware. This new solution functions the same way as Forefront. Other than a different icon, you probably won’t notice a difference!
About the Installation
- Microsoft’s System Center (the engine behind the new Microsoft Endpoint Protection) will be deployed to Windows computers running the LANDesk agent. When this happens, you can ignore a pop-up alert from Forefront indicating that new software is being installed. After System Center installs in the background, a new folder is created under “All Programs” called “Microsoft System Center 2012 R2” which you can also ignore.
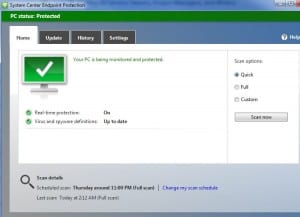 As soon as Microsoft Systems Center installation is complete, Forefront will be uninstalled and Endpoint Protection will be deployed to the computer. This process will cause two alerts to pop-up on your computer screen which you can safely ignore. The first indicates that you need to update Forefront, and the second states that you need to install antivirus software. Endpoint Protection will complete shortly after the two pop-up messages appear, and you’ll see new system tray icon.
As soon as Microsoft Systems Center installation is complete, Forefront will be uninstalled and Endpoint Protection will be deployed to the computer. This process will cause two alerts to pop-up on your computer screen which you can safely ignore. The first indicates that you need to update Forefront, and the second states that you need to install antivirus software. Endpoint Protection will complete shortly after the two pop-up messages appear, and you’ll see new system tray icon.
The deployment is under testing within OIT. We are scheduled to complete the test rollout on May 15. Following the successful implementation, the deployment task will be approved for all SMU Windows machines.






