 And that’s a wrap!
And that’s a wrap!
You did it!
You made it to the end of the Biggest Phisher!
You are now one of the most highly trained phish spotters ever! Throughout the month, you received 22 of the most challenging phishing messages we’ve ever sent here at SMU. Overall, 93% of the time, y’all didn’t click… and y’all kept getting better throughout the month!
At this point in the email, I usually insert the leaderboard. But you’ll have to tune in on November 5, 2020, at 1 p.m. to find out the winners! (You don’t have to be present to win, I’ll let you know either way). It was a real nail biter right up until the end.
Thank you again for being a part of this! I hope you had some fun.
October 23: Salary Update
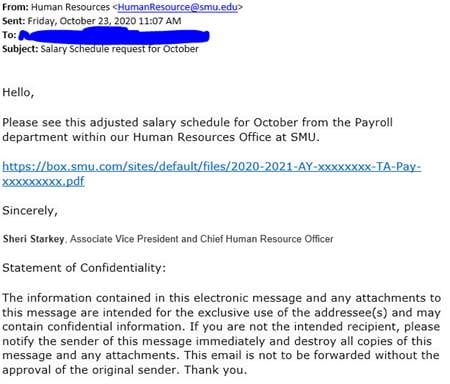
This one surprised me… This was actually tied for the 3rd most successful phishing message of the month! The address looked legit, but if you hovered over, the real URL was smu.directory/box.com. Remember you always have to look at the leftmost part of the address…everything after the “/” is just there to distract you.
October 26: Job Opening at UTD

It looks like you’re not a good fit for this phishing message. I was sure this one would be more successful. It’s very similar to what a real Glassdoor alert might look like, however, this was the least reported phishing message of the month, probably because we are so desensitized to seeing regular alert messages like this…
Context is always key! If you’re not expecting something, it’s best to go to the real source…which many of you did by going to Glassdoor.com and doing your own search! I’m so proud of you!
October 27: You Got a Voicemail from Me

If you were wondering what kind of spear phishing messages that cybercriminals use to target me specifically, this is it. I copied most of this directly from a real phish I received. But you guys picked up on it almost immediately because of how different it is from our real voice mail messages. The hacker in this case was probably just guessing at our voicemail format, but it’s possible that future campaigns could be closer to what we actually use or to embed a malicious file instead of a real recording.
October 28: Your Library Book Isn’t Overdue

If you had a library book out, you might have been worried. But most people were able to identify that the link was tricky, but didn’t come back to SMU: Library-services.com/smu.edu. The campaign also used the name of the former dean of the Libraries…this is a good red flag to alert you since cybercriminals may not have all the most up to date information when they do their research.
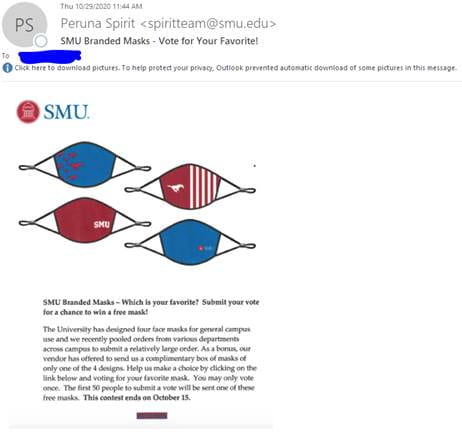
October 29: Vote…on your favorite mask
This campaign was a little unique in that the email only contained a picture… To see the image/text, you had to allow images to be displayed. But the whole picture was a clickable link that could take you to a malicious page. It turned out this technique became one of the most effective campaigns because of it!
October 30: Faculty Evals

This phish was based on a real phishing campaign targeting another University. It’s actually the same form that Google will send you if you sign up for Google Forms, with the links modified. I tried to trip you up a bit with the URL… smu.email/gmail.com. smu.email is a domain we registered for this game, but it could have been any malicious domain…so remember to look at the beginning of the URL first.
Some of you reported the email address since it was a Gmail address. But this also came from a real email scam using real names of people inside SMU with fake Gmail or other free email domains.
George Finney, J.D.
Chief Security Officer



