 It was an exciting week with a lot of movement on the leaderboard, but we’re back to a nine-way tie for first! There’s a seven-way tie for second and a six-way tie for third, so this is still anyone’s game!
It was an exciting week with a lot of movement on the leaderboard, but we’re back to a nine-way tie for first! There’s a seven-way tie for second and a six-way tie for third, so this is still anyone’s game!
I’m also excited to let you know that my new book on cybersecurity, Well Aware, is coming out next week. I’ll technically be out on vacation for the book launch, but I’m having so much fun with this project I’ll still be logging in to keep track of the scores and send you updates. So, if you see an out of office message from me, it’s not a phish! Don’t worry though, keep the reports coming in!
The Leader Board
| Place | Codename |
|---|---|
| 1st | Britney Spearphish |
| 2nd | Turkey |
| 3rd | SneakySniffer |
| 4th | tech0ne |
| 5th | Sally Ride |
| 6th | Valkyrie |
| 7th | Obtuse |
| 8th | Yorky Lover |
| 9th | Emtrek |
| 10 | phishfood |
October 9: HR Benefits

I totally thought that more of y’all would have fallen for this one…so kudos to you for totally breaking my expectations! A lot of phishing is actually very timely, and since October is usually around the time that HR’s Open Enrollment and HR Fair are being discussed, this fell around the same time as those were being discussed. But you guys instantly realized that this was way out of the ordinary for an HR communication. Lots of red flags to recognize with this one.
October 12: Tested Negative

This phish was highly successful, but it would have been even more devastating if it had said a close contact had tested positive instead of attempting to be humorous and saying your contact tested negative. The COVID-related phishing messages have been some of the most successful campaigns of the competition because of the fear and urgency we rightly place on this pandemic. But we also know that the FBI has reported phishing is up by over 800% since the pandemic began and the bad guys are using this as an opportunity to take advantage of us.
October 13: Prime Day
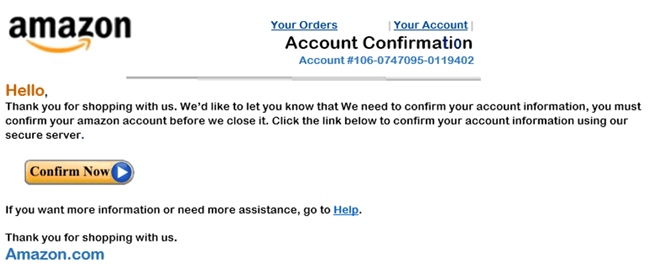
It was Prime day on Monday and Tuesday, which made it the perfect time to bring up the old Amazon account confirmation notice. Had this not been a simulated phish, you might have been directed to a fake Amazon login screen which would have tempted you to give away your username and password. Pro tip – if you ever do accidentally click here, there is still a dead giveaway that can help you not put your password in. If you have your phone or browser remember your username and password, when you hit a fake login page, your browser won’t prompt you to use a stored password because you’ve never been to that site before.
October 14: I did not change my password
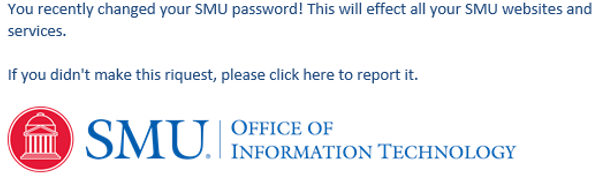
This was the classic password change phish. The twist was that we were asking you to confirm that it was you, and since you hadn’t changed your password, you may have felt some pressure to click right away to fix something. The timing here was intentional…sending the phish in the early morning hours might have been a trigger that a hacker was pulling an all-nighter to lock you out of your account.
October 15: All I wanna do is Zoom a Zoom Zoom Zoom

We didn’t get enough entries to send phishing for the whole month, so I’m proud to say that this one was my personal contribution to the effort. I’m not eligible to win, but I’m happy to be able to say that the old man still has it. It wouldn’t have been the most successful phish, but about 12% clicked. This one used an appeal to authority, but most people would have been suspicious if we used Dr. Turner’s name, so we used Provost Loboa’s instead. This is also another example of a typosquatting domain, the normal URL for zoom is Zoom.US, but we used Zoom-en.net. I think the thing that caught most folks was actually the timing, since we sent it right at 2pm, the panic of having the Provost waiting on a call created a sense of urgency.
George Finney, J.D.
Chief Security Officer



