By Rajat Shetty During the holiday season, Cybercriminals’ potential victims are often caught up in the frenzy of shopping, finding the best deals, and acting quickly to take advantage of limited offers. Email and social networks are clogged with sales and offers, both legitimate and fraudulent. Sometimes haste causes shoppers to miss the warning signs of a fraudulent website.
Avoid Suspicious Websites
Make sure you cross check the contact info before submitting your payment details. In many cases, fake websites put up incorrect contact info like a wrong phone number or an incorrect address. A few other warning signs of suspicious websites are lots of broken links, grammatical mistakes, and spelling errors. If in doubt, don’t check out!
Verify the Web Address (or URL)
Before you type in any credit-card numbers at check out, check the Web address, or uniform resource locator (URL), of the payment page and make sure it’s using a secure connection. You should be seeing either the character string “https://” before the website URL, or a small icon of a green padlock. Also, make sure the URL address is correct, and not a slight misspelling of the real address or a random URL.
For example, check the snapshots below for the official website of Beats headphones. The first one is the original website, whereas the second website is a fraudulent one having the exact layout and font style as the original website. The difference is, when you pay through credit card or debit card on the 2nd website you are not going to receive any headphones (Not even a fake one!)
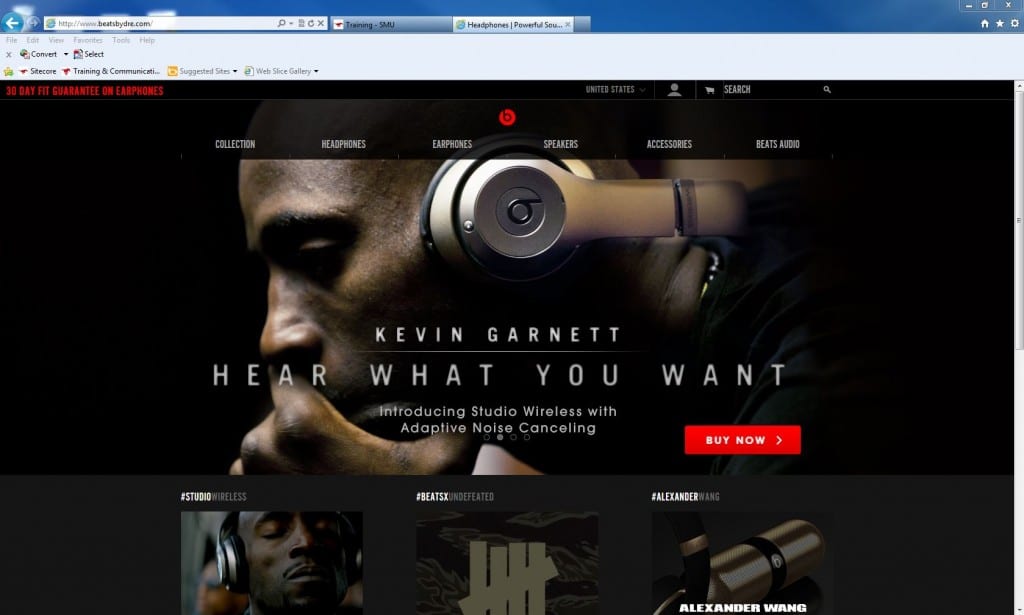
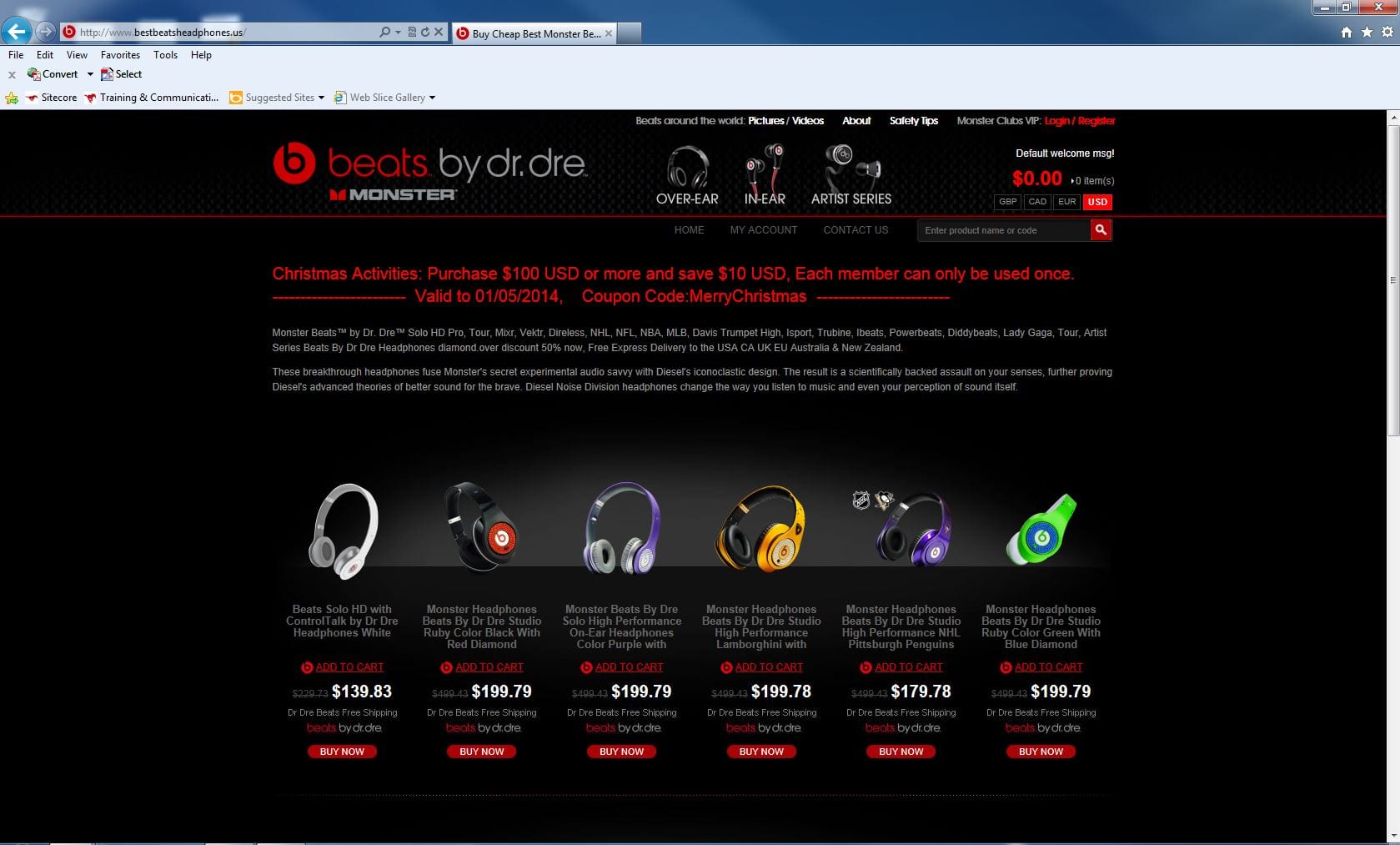
Use Caution when Shopping by Phone
Although it can be convenient, use extra care when shopping with your smartphone. Phones are more susceptible to malwares as most do not have an anti-virus. Also, it’s highly unsafe to store your credit card or debit card information on your phone. Only buy from trusted and familiar websites when you shop through your smartphone, and use a password protected internet connection. Never shop over unsecured public Wi-fi. Remember, it’s always better to check twice before clicking the ok button. People loose thousands of dollars in a haste to snag online deals. Protect yourself from becoming a victim to fraudulent websites by exercising caution before giving out your credit/debit card details.






