 You guys are amazing. You’re catching so many phish… I’m blown away! Who knew stopping phishing could be so much fun:) The leaderboard has been pretty stable this week… mostly because you are all so good. This means it’s still ANYONE’s game.
You guys are amazing. You’re catching so many phish… I’m blown away! Who knew stopping phishing could be so much fun:) The leaderboard has been pretty stable this week… mostly because you are all so good. This means it’s still ANYONE’s game.
The Leader Board
| Place | Codename |
|---|---|
| 1st | Turkey |
| 2nd | phishfood |
| 3rd | Sally Ride |
| 4th | Valkyrie |
| 5th | Obtuse |
| 6th | Anglo |
| 7th | Britney Spearphish |
| 8th | Phyling Phish |
| 9th | Emtrek |
| 10 | SneakySniffer |
Question of the Week
Mandarinfish asks, “When we receive emails that are sent out to a distribution list that we didn’t, or did I suppose, sign up for, how can we be sure that the unsubscribe link isn’t a malware link? I’m always hesitant to unsubscribe to email lists because I’m worried it won’t be safe.”
Personally, I never click unsubscribe. You are correct that the link could be malicious. But also, it confirms that your email is still a valid address. Unsubscribing just means they can’t send email to you (assuming they follow the rules), but that doesn’t mean they have to delete you from their database altogether. The only thing that they can do to make money on your name at that point is to sell your email address.
Y’all asked for a summary of the phishes you got, so here goes…:
October 2: The COVID Update.

This was deceptively simple, which made it the most successful phish so far. For folks that haven’t signed up, if you go to the blog, and you’ll get daily email updates to go to SMU’s COVID dashboard…not everyone has signed up for that, which limited the success of this one. This one was hard…about 1/3 of the folks clicked…but it wouldn’t be fun if it wasn’t a challenge! What makes this a good phish is that sometimes cybercriminals can read our user’s email, and just like we did, craft a message that looks almost exactly like one we might expect to get…so it’s important to look for other cues that seem different. The link went to a URL that had SMU in it, but the real daily update comes from Blog.SMU. The from address was also not the same as the usual ones.
October 5: SMU Athletics

I will admit that I updated the template a little to reflect our current 4-0 status. The link went to what is known as a typo-squatting domain. Our real athletics site is smumustangs.com, but I was able to register smu-mustangs.com. Lots of folks spotted the “Spooky Express” thing, which we played up since the game with Navy will happen on Halloween, but in reality, SpookyExpress is a gambling site that created the image.
October 6: Dropbox.

As a University, we share information through Box, however, there is another provider out there that provides the same service called Dropbox. We chose another typosquatting domain for this, inverting the “p” to a “q”. We see a LOT of real phishing activity that mimics file share or similar sites that all try to get you to click or download a file with malware, the most common are: fake Google Drive, fake voicemails, fake eFax requests, or even fake notices from FedEx. We included a name, Jennifer, to give it a little extra incentive, since everyone knows at least 1 Jennifer, but many of you found this to be the thing that jumped out at you most as a red flag.
October 7: iOS update.
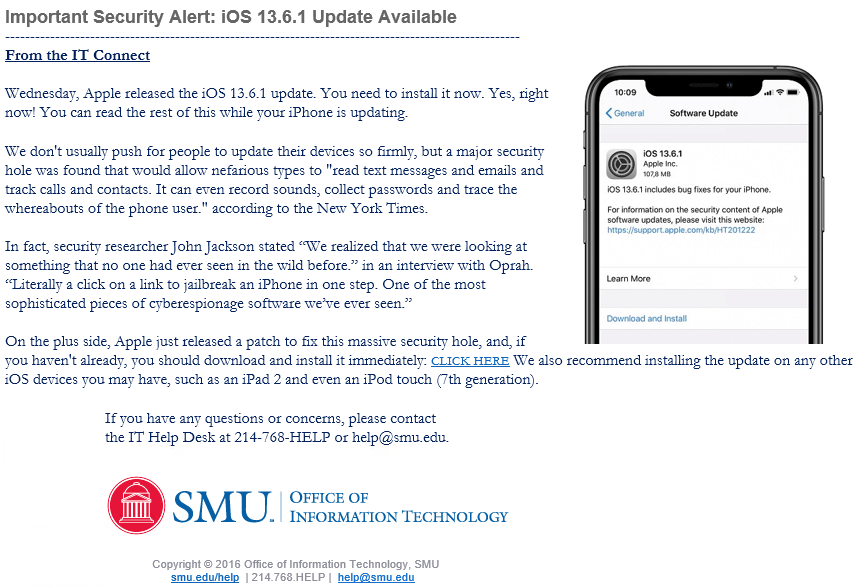
This phish was written before the latest iOS release came out, which is 14.0.1… Click Here to install that. Just kidding. But also, as far as I know, Oprah has never been quoted about the security issues in an iOS update. We’ve seen a lot of phishing attempts that leverage the urgency of an IT security issue to trick you into clicking. You guys seemed pretty prepared for this one…this was actually the least clicked campaign so far.
October 8: HR.

Wrong email address. Weird URL. Lots of folks mentioned that they just had a meeting with their supervisor and they would have mentioned this.
You guys are doing awesome…keep on not clicking.
Security starts with YOU!
Thanks,
George Finney, J.D., CISM, CISSP
Chief Security Officer



